What is Password Hash? How does it work with AD Connect?
As you know, companies that partially move their resources to the cloud synchronize their on-prem Active Directory users to the cloud environment for easier access to these applications. In this scenario, many organizations are concerned about the migration and storage of user credentials. Many questions about password security such as “How is the password sent to the cloud”, “Where is it stored” need to be answered. Knowing the steps that the data goes through while being transferred or stored will minimize the worries in this regard.
Based on this, I wanted to both write about the password hash method and discuss the relationship between Azure AD Connect and the password hash.
If we start with the password hash; How does Password Hash work?
Password Hashing is actually a mathematical method used to complicate data. It is a method generally used when you want your password not to travel within network packets or leave the device, company network or your own ecosystem. After you enter your password, it becomes a complex value with the help of an algorithm. This value, which we call hash, is defined and stored in the database instead of your password. The password you use when you want to log in is hashed again and compared to the previously defined hash to the database. Thus, you complete the login process without your password itself being stored in any database or included in the network package.
When hashing passwords, the same inputs always give the same output. For example , Tayf1234 value hashed according to MD5 algorithm is always as follows: d21e4f2944d0e3bc8ebafb28fac5e4166c
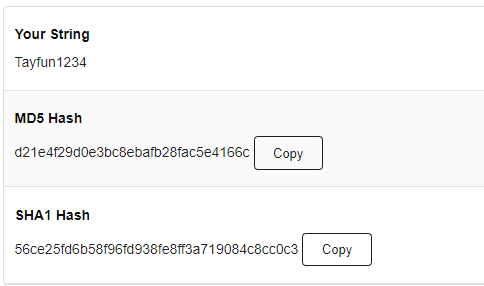
But even a small change of one character transforms the output into something else entirely. For example: Hashing Tayn1233 with MD5 yields the following value : 145d9ceb54c33a06ff57926ab78ff63b778
As you can see a single character leads to a completely different output.
Although password hashing is a one-sided method, since the same inputs give the same outputs, it is always possible for your password to be guessed at some point or to be cracked by attacks prepared for this purpose. If you have used a common or simple password, it will not be too difficult to decode your password, as the hash of this password is a very common hash before. There are even websites that are used to decode the hashes of well-known passwords like this one. However, if you are using an unusual and complex password, dictionary or combination attacks will become an expensive and time-consuming method of cracking your password. Although it is still possible for your password to be stolen, it will become a remote and unlikely possibility.
In order to minimize this possibility and prolong the duration of brute force attacks based on trial and error, many authentication services use the Salt method.
In the salting method , a few random characters are added to the end of your password before it is hashed and stored. Password hashed this way becomes more difficult to crack. Moreover, even you know half of the hashed password. 
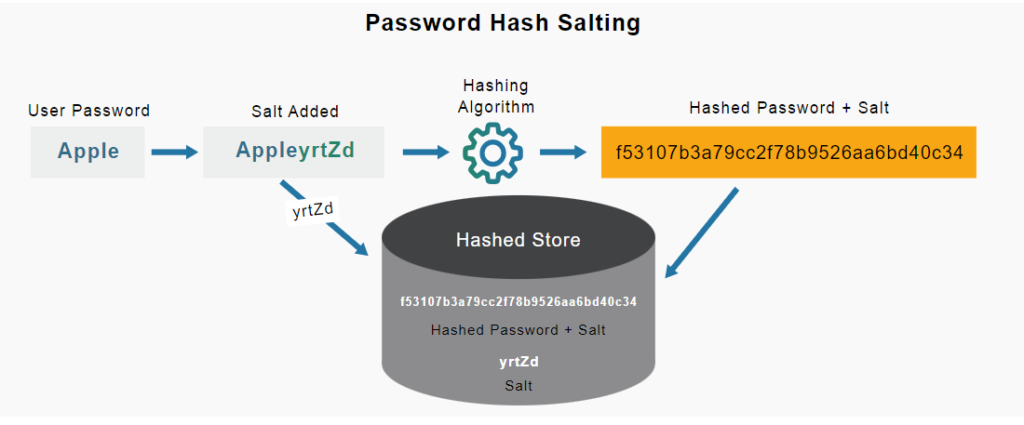
The three most important benefits of the salt method are:
1- Brute force attacks by attackers will take an unbearable time because it increases the complexity of the password and therefore the hash.
2- Even if the hash is captured somehow, the attacker will not be able to access the original password.
3- Even if the hash is captured, the attacker cannot associate this hash with other user accounts using the same password, since the original password cannot be reached over this hash.
When using this method, Salt can be appended to the beginning or the end of your password.
If you want to make things even more difficult for the attackers, we also have pepper on our menu. In the Pepper method, a character is added to the password before it is hashed, very similar to the Salt method. However, this character is not stored in the database, unlike Salt. Neither the user nor the database is aware of this secret character. The secret character is only in the source code of the website.
For example, if the password is Tayf1234 , the character M is added to the end . However, since this M character, pepper, is not stored in the database, the system tries all upper and lower case letters one by one at every login. In fact, for an end user, this is not a very long time, but for a hacker trying different combinations, it means a huge waste of time.
To optimize password security, the hash process should be designed as Password+Salt+Pepper .
Role of Password hash on AZURE AD
Password Hashing is a feature of the Azure AD Connect application used to synchronize your local Active Directory directory to the Cloud environment. Users' login to local applications and Microsoft Cloud services with the same password both creates comfort for users and reduces the effort of your helpdesk team. To achieve this, you need to synchronize all or some of the users on Active Directory to the cloud environment. However, during this synchronization, called "Directory sync", synchronizing users' passwords and storing them in the cloud environment is not a smart method. For this reason, you should activate the "password hash" feature when configuring the Azure Active Directory Connect application.
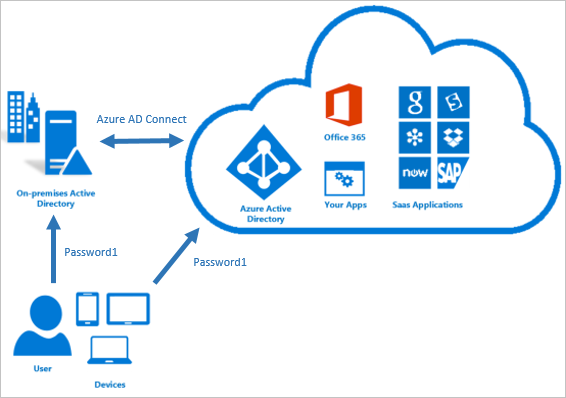
How does the Azure AD Connect Password hashing process work?
While synchronizing the passwords of on-prem users to the cloud environment, Sync Engine ( AD Connect ) plays the leading role. AD Connect sends a replication request to the Domain Controller (DC) in the environment. DC responds to this request as an old-fashioned MD4-encrypted hash. Sync Engine, which receives user information, encrypts this data with a more modern method and generates the hash value.
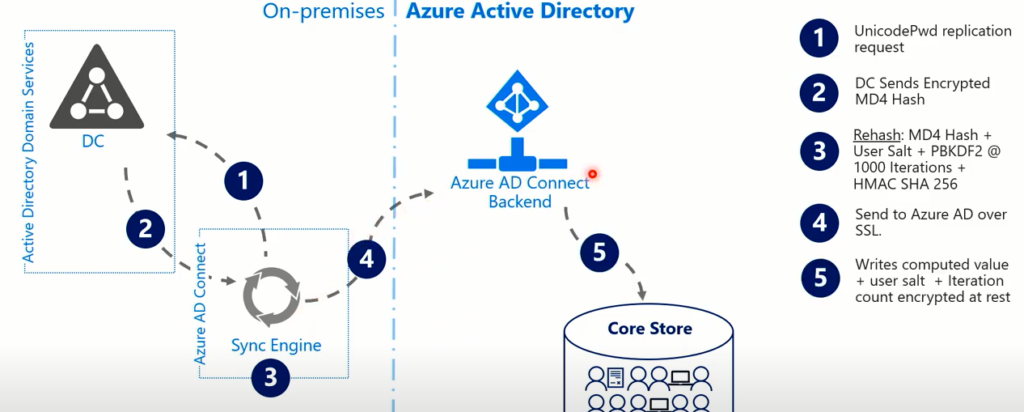
After converting the data received from the DC to a 64-byte value, it adds a 10-byte salt. This value is hashed again with encryption methods such as PBKDF2, HMAC SHA 256, and 32 bytes of data are obtained.
Then, AD Connect does its last duty and sends this data, that is, the hashed version of your password, to Azure Active Directory using SSL. The hash of your password is stored here by being encrypted (bitlocker) on a storage basis.
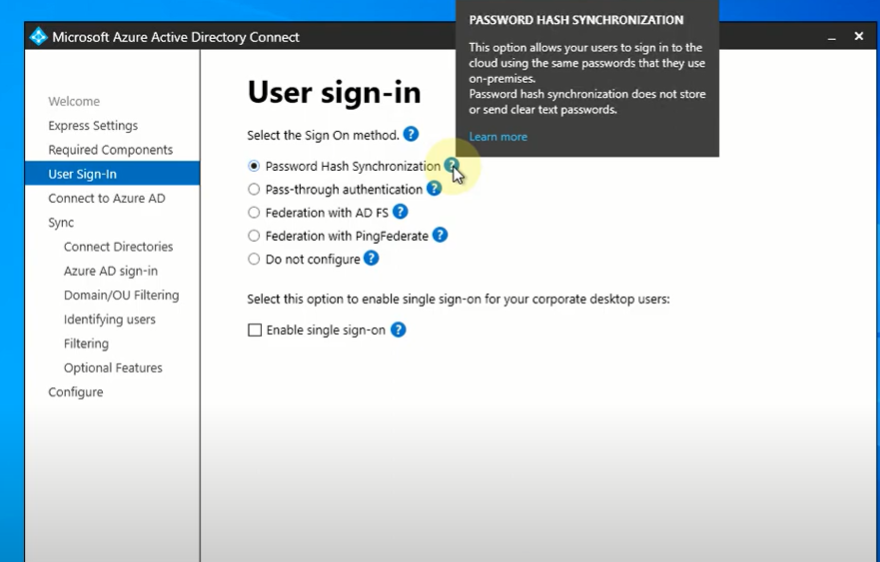
So, how do we activate the Password hash on Azure AD Connect ?
When installing AD Connect, it will be sufficient to tick the Password Hash Synchronization option in the User sign-in section.
I hope this has been enlightening about Azure AD Connect and password security. If you have a question about this topic, you can share it in the comment section.
Comments
Post a Comment